How to Secure Your WordPress Website Against AI-Powered Hacking in 2026

Hackers aren’t just guessing anymore—they’re using AI.
Every day, WordPress sites are being scanned, tested, and attacked by AI-powered tools that move faster than any human hacker.
If your site isn’t protected, one small mistake—like an outdated plugin or a weak password—can give hackers a way. And most website owners don’t even notice until the damage is done.
Through this blog, I want to help you understand how AI hacking actually works in 2026, and more importantly, how you can secure your own website against it.
Let’s dive in and make sure your WordPress site stays safe.
AI + Hacking: Before and after
Think of the difference between a single thief trying to open a door compared to an army of robots testing every lock in the city simultaneously.
Previously, hackers often hit limits set by human speed and attention—they needed to sleep, grew bored, or moved on after targeting a few sites.
Now, AI changes the scenario. AI-driven bots don’t get tired or distracted – they can continuously scan every inch and detail of a website, 24/7.
So, this means attacks that used to take weeks or months can now happen in minutes.
| What changed | Before gen-AI (≈2021–2022) | After gen-AI (2023–2025) | Source |
| Time to craft a convincing phishing email | ~16 hours by a human team | ~5 minutes with gen-AI | IBM X-Force write-up. |
| Volume of phishing emails | Baseline (pre-ChatGPT) | +1,265% since Q4 2022; ~31,000/day mid-2023 | SlashNext report; Security Magazine coverage. |
| Password cracking speed | Traditional lists/rules took longer | AI (PassGAN) cracked 51% of common passwords in <1 minute; 65% <1 hour | Tom’s Hardware summary of Home Security Heroes study. |
| Exploit speed after disclosure | Days–weeks to appear at scale | Active exploitation observed within 24–48 hours in major cases | CISA advisories on rapid exploitation (e.g., Ivanti). |
| WordPress vuln landscape | Ongoing plugin exposure | 6,700 new WP vulns in H1-2025; 41.5% judged “exploitable in real life” | Patchstack mid-year 2025 report. |
| Quality of phishing content | Easier to spot errors | National agencies warn that AI makes scam emails much harder to detect | UK NCSC warning (The Guardian coverage). |
AI-related WordPress website security hacking stats
WordPress is the world’s most popular website platform – and unfortunately, that makes it a popular target for hackers. To understand the scope of the threat, let’s look at some numbers:
| Metric | Statistic |
| Attacks on WordPress (per minute) | ~90,000 attack attempts/minute worldwide. |
| WordPress sites hacked daily (est.) | ~13,000 sites per day (about 9 per minute). |
| Share of hacked websites running WordPress | ~95% of infected CMS sites in 2022 were WordPress. |
| WordPress vulnerabilities in plugins | 52% of WP vulnerabilities are in plugins. |
| Hacks involving an outdated WordPress install | 44% of hacked WP sites were running an old version. |
How hackers use AI for website attacks (and how you fight back)

Let’s break down the major ways hackers are using AI to attack websites, especially WordPress sites, and what you can do for each. We’ll describe what each attack is, how AI makes it more potent, signs that it might be happening to you, and how to defend yourself.
1. Automated audit bots: AI “Scans” websites for weak spots
Automated audit bots are AI-powered tools hackers use to “scan” websites for weak points before attacking. These bots explore your site, gathering details like which plugins you use, existing usernames, or hidden files.
Traditional bots just fetch pages, but AI bots are smarter—they can read your pages and URLs intelligently.
For example, they might spot “/wp-admin” or known plugin file patterns and recognize the exact plugins and versions on your site. This helps hackers quickly fingerprint your WordPress setup and find weak spots.
Also, AI bots work very fast, scanning thousands of sites simultaneously, while a human hacker would take hours per site.
Signs your site is being scanned:
- Sudden spikes in traffic or strange requests in your logs.
- One IP address rapidly accesses odd URLs like plugin readme files or admin-install pages that regular visitors wouldn’t use.
- User agents with strange or generic names (often bots).
- A high volume of requests is hitting sensitive or hidden URLs, especially at unusual times.
How to protect your site:
- Use a strong firewall or security plugin that limits the rate of requests.
- Block or slow down IPs that access many pages quickly.
- Add a robots.txt file to guide well-behaved bots away from sensitive parts, although bad bots might ignore this.
- Hide or remove version information that plugins sometimes reveal publicly.
- Set up “honeypot” links—fake admin or data URLs that real users don’t visit, but bots might.
- When accessed, these can signal a bot and allow you to block it.
- Regularly check your access logs to catch unusual scanning activity early.
💁 Related reading: How to Use Website Heatmap in WordPress (with Microsoft Clarity) – Read more
2. Credential attacks: They guess or reuse passwords (now with AI muscle)
Credential attacks happen when attackers try to sign in using stolen or guessed usernames and passwords. They use leaked passwords from other sites (credential stuffing) or try many common passwords until one works (brute force).
About 80% of breaches involve weak or reused passwords, so the login page is a common target.
AI makes these attacks faster and smarter. Instead of guessing blindly, AI studies leaked passwords and learns real patterns. Tools like PassGAN pick the most likely passwords first. That lets them crack many common passwords very quickly.
AI also spreads attempts across many IP addresses to hide the attack. It can focus on common choices (like “abc123”) and even adjust guesses if part of a password looks right.
How to defend your website from these credential attacks:
- Use strong, unique passwords for all accounts, especially admin.
- Enable multi-factor authentication (MFA) to block access even if passwords are guessed.
- Limit login attempts with plugins to lock out an IP or user after a set number of failures.
- Change the default login URL (rename /wp-login.php) to reduce noise from generic bots.
- Use application-level or cloud firewalls that detect and block credential stuffing patterns, stopping attacks before they reach your site.
3. Phishing & social engineering: AI writes scarily convincing fake messages
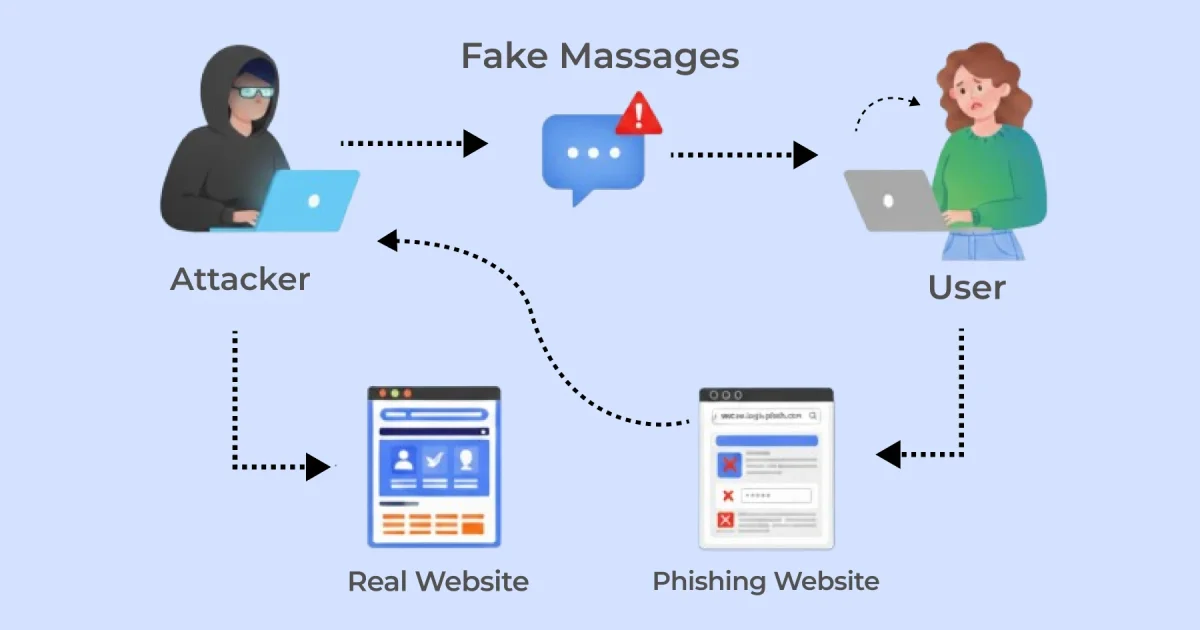
Phishing is when attackers trick people into giving up sensitive information or access, usually through fake emails, social or websites. AI can produce many variations of the same phishing email to evade spam filters—a technique called polymorphic phishing.
For example, you might receive an email pretending to be from your hosting company or bank, asking you to log in to a fake site or share a password. Attackers may also create fake login pages that mimic your site to steal user passwords.
AI language models like GPT-4/5 make writing convincing phishing emails easy and fast. AI also translates phishing messages into multiple languages and designs fake login pages mimicking real websites perfectly.
Signs of AI-generated phishing:
- Emails creating urgency or asking for sensitive info are unexpectedly.
- Well-written messages without typical spelling or grammar mistakes.
- Suspicious links (hover to check where they lead).
- Sender addresses that are slightly off or fake.
- Generic greetings instead of your name.
- Fake site URLs that look similar but are wrong (e.g., mywordpress-security.com vs wordpress.com).
- Unrequested login alerts or password resets.
- Reports from users about odd messages pretending to be from you.
How to protect yourself and your website from this:
- Set up email security protocols like DMARC, SPF, and DKIM to reduce spoofed emails.
- Train yourself and your team never to click login links in emails—always visit sites manually.
- Remember, official organizations like WordPress.org rarely contact users directly.
- Use password managers or browsers that alert you about suspicious login pages.
- Monitor the web for fake domains that impersonate your site using brand monitoring services.
- Encourage users to enable two-factor authentication (2FA) so attackers can’t log in even with stolen passwords.
💁 Related reading: The Ultimate WordPress Security Guide – Best Practices- Read more
4. Malware & payload generation: AI helps craft sneaky malicious code
Malware is harmful code that hackers leave behind after breaking into your site.
In WordPress, this can appear as rogue PHP files hidden in uploads, infected theme or plugin files, or malicious scripts injected into the database.
AI enhances malware by generating sophisticated scripts, such as those that steal user passwords and email them, surpassing the abilities of less skilled hackers.
Some AI-driven malware can even adapt after detection, rewriting or re-encrypting itself to evade scanners. AI technology also supports the creation of numerous unique variants of malware, phishing platforms, and exploit code, which further complicate detection.
Warning signs of malware infection- heading
The signs of malware remain similar – unusual files on your server, modified files, unknown admin users added to WordPress, or your site suddenly sending out emails or links you didn’t put there.
If an AI-generated malware is present, you might notice slightly odd things like files with random names
(e.g., wp-content/plugins/securiry-plugin/gyhftrh.php – notice the misspelling of
“security” could be deliberate) or base64 encoded chunks in PHP files (often used to hide contents).
Strategies to defend against AI-driven malware
- Use reputable WordPress security tools to scan core files, check plugin and theme files, and keep scanners updated.
- Add a Web Application Firewall (WAF) to block malicious requests and uploads.
- Restrict file permissions to limit who can edit or upload files.
- Disable file editing in WordPress by adding define(‘DISALLOW_FILE_EDIT’, true); to wp-config.php.
- Use a Content Security Policy (CSP) to limit which domains scripts can run from.
- Pre-scan uploaded files using hosting providers or security tools before they reach your site.
- Apply a layered defense strategy: multiple security layers catch malware if one fails.
- Keep regular backups as your ultimate safety net if malware bypasses all defenses.
5. Security & defense bypassing: AI learns your security rules
Security and defense bypassing is a modern hacking technique. When attackers or bots hit your security defenses (like firewalls or brute-force protections), they don’t just give up—they adapt.
👉 Imagine AI as a player in a game where the goal is to “get past the firewall.” If one malware snippet is blocked, the AI rewrites parts of it and attempts infiltration again, remembering what worked.
For example, if your site blocks <script> tags, AI might switch to a less obvious method like an <img onerror> injection.
Defensive strategies against AI-driven evasion
- Use multi-layered, dynamic security combining WAFs, behavior-based detection, and manual review.
- Employ security tools with machine learning to recognize persistent, varying attacks and ban suspicious IPs.
- Regularly update firewall rules and signatures to outpace AI learning.
- Add temporary or aggressive blocking rules when unusual probing is detected.
- Use rate limiting across IPs, sessions, and globally to catch slow or distributed attacks.
- Rotate or randomize security parameters like honeypots or blocked inputs to prevent attackers from learning fixed patterns.
- Stay updated with threat intelligence feeds to defend against the newest evasion techniques.
6. Data scraping & privacy attacks: “AI hacking customer data fast”
Data scraping involves automated tools copying content or data from your site without permission.
For example, on an e-commerce WordPress site, attackers might scrape product prices to undercut you or collect user profiles to target for spam or scams.
Account takeover (ATO) bots use stolen credentials to hijack user accounts, then scrape personal data or commit fraud.
Once an account is broken into, AI can read private messages or pretend to be the user in scams, making things worse. This automation makes stealing data much faster and easier than doing it by hand.
Signs of data scraping and ATO bots
If someone’s scraping your site heavily, you might see unusual traffic patterns.
When you see a single IP (or a small range) systematically going through your site’s pages at a faster rate than any human visitor would – like hitting every user profile page alphabetically, or every product page in a category.
Another sign is competitor or weird sites having your exact data – e.g., you find a clone of your site or someone else mirroring your content (they likely scraped it).
Also, if your site sends out confirmation emails for data exports or password changes, a surge in those could hint that someone is systematically taking over accounts and extracting data.
How to protect your site from scraping and ATO bots:
- Limit public data exposure and lock down open APIs or require authenticated access.
- Use CAPTCHA and bot detection tools to block basic scrapers.
- Implement rate limiting on page requests per IP.
- Employ bot management through CDNs or WAFs to distinguish bots from humans.
- Set “honeytokens” (fake data points) to detect and block scrapers if accessed.
- Educate users to use strong, unique passwords and enable two-factor authentication (2FA) to prevent credential-based ATO.
- Monitor for suspicious login activity such as many accounts accessed from a single IP.
- Force password resets and session invalidation for compromised accounts.
- Minimize publicly visible sensitive user data to reduce scraping incentive.
- Consider legal deterrents like Terms of Service forbidding scraping and user-agent traps delivering legal notices.
7. Supply-chain & dependency attacks: “AI finds vulnerable plugins and packages”
A Supply-chain & dependency attack is when hackers don’t attack your site directly — they attack the software or services your site depends on.
👉 In simple terms: instead of breaking into your WordPress site, they break into a plugin, theme, library, or service you use. Once that trusted tool is compromised, the bad code comes into your site automatically.
AI can scan through huge amounts of code, plugin versions, and security reports much faster than a human. It compares what your site is running with known security issues.
Example: If your site is using Plugin Y version 1.2 and security reports show that version has a serious flaw (which was fixed in version 1.3), AI can spot this quickly. Hackers then target sites still using the old, unsafe version.
Defense against supply-chain attacks
- Keep WordPress core, plugins, and themes updated promptly—enable auto-updates or schedule daily checks.
- Remove unused plugins and themes to minimize attack surface.
- Subscribe to vulnerability alerts from sources like Patchstack or Wordfence, or use security plugins that notify you of known vulnerabilities.
- Use least privilege file permissions and configure your site securely to limit damage from vulnerabilities.
- Employ web application firewalls (WAFs) and consider “virtual patching” that blocks known exploit signatures at the network level.
- Test new plugins in staging environments before deploying them live.
- Track and update external libraries or scripts your site depends on.
- Stay proactive with monitoring, integrity checks, and layered defenses to catch attacks early.
💁 Related reading: WordPress Security Checklist: Plugins, Updates, Backups. Read more
What’s coming next: The future of WordPress security & AI
AI is quickly becoming both helpful and risky in cybersecurity. On one side, attackers are using AI to speed up and improve their attacks – we’ve already seen AI-powered phishing, quick password guessing, and bots that can learn and change. On the other side, defenders are using AI too, to spot and stop attacks.
The future of WordPress security will likely feel like an AI vs AI battle, as one report put it: a digital game of “Robots vs Robots” with both sides using AI against each other.
This means we can expect attacks to get faster and more advanced, but also expect security tools to get smarter.
If you stay on top of updates and leverage good security tools, you’ll be in a strong position to ride this wave.
Frequently asked questions (FAQs)
Q: Can AI hack my WordPress site on its own?
AI isn’t a “thinking hacker,” but it’s a powerful tool. Hackers use AI bots to guess weak passwords, scan plugins for flaws, or send fake messages—much faster than humans. If your site has obvious gaps, AI-driven attacks can find and exploit them quickly. Strong passwords and regular updates remove easy targets.
Q: My site is small. Will AI bots still attack me?
Yes. Bots scan the whole internet, not just big sites. Small sites are often easier to hack because they’re less maintained. Hackers don’t cherry-pick—they hit any site with weak security. Basic protections like updates, strong passwords, and a security plugin make bots move on.
Q: I’m not technical. How can I protect my site?
Start with simple steps: use a security plugin, enable automatic updates, set up two-factor authentication, use strong passwords, and keep backups. These basics stop most AI-driven attacks. Think of it like car care—you don’t need to be a mechanic, just do routine maintenance.
Q: Do I need AI-powered security tools?
Most security plugins and services already use AI or machine learning behind the scenes. Tools like Wordfence, Sucuri, or Cloudflare analyze traffic and block threats automatically. You don’t need to buy something labeled “AI security.” Just use a trusted plugin and host—they’re already using advanced defenses.
Q: If I keep WordPress and plugins updated, am I safe?
Updates close most security holes, but no site is 100% safe. New flaws appear (zero-days), and AI bots can also exploit weak passwords or bad settings. Updates are your first shield, but combine them with strong credentials, backups, and security plugins for layered protection.